Table of Contents
ToggleLast Updated on March 14, 2022
CPanel security how to go about it? It is important to Keep your local environment updated and virus free.Therefore you must tighten the security of the cPanel of WordPress site to prevent any kind of hacking.
In This WordPress tutorial you will learn more about how to protect Cpanel by adding an additional layer of security to your WordPress. Find list of cPanel Security Measures to Secure Your cPanel Server and Improve Your WordPress Security.
Here, you will learn how to improve and optimize your cPanel server to prevent from security breaches, attacks and other security problems that you can find on cPanel.
There are two groups for security, applications native to cPanel and software solutions that we can add.
With a default installation of cPanel, the security of that is configured at the minimum, no server service will be really configured as it should protect you from attacks on your websites or on your server directly.
Natively cPanel offers some interesting tools which are in the “security center” but we will also show you how to install applications in order to secure your server and sites as much as possible.
All the configurations will help you fight security issues and in some cases even send you alerts in the event that an IP address is attacked.
Can cPanel be Hacked?

You can gain access to your cPanel account remotely through Secure Shell (SSH). If you can, so can a hacker. Examining your server logs is an extremely effective method of finding out if your site has been hacked.
Your logs are in your cPanel, which you can access by logging into your Customer Space. In cPanel, under Statistics, you will find 2 different types:
- Accessibility logs: these will tell you who accessed your WordPress and from which IP address.
- Error Logs: These will show you what errors have occurred whenever your WordPress system files have been modified.
Using the information provided by your server logs, you can check if your WordPress site has been hacked or not ( you can also use any wordpress malware scanner from here. And since they also keep track of all IP addresses used to access your website, you can blacklist or block any unknown IP addresses that are not from your location.
How to secure Cpanel server from hacking?
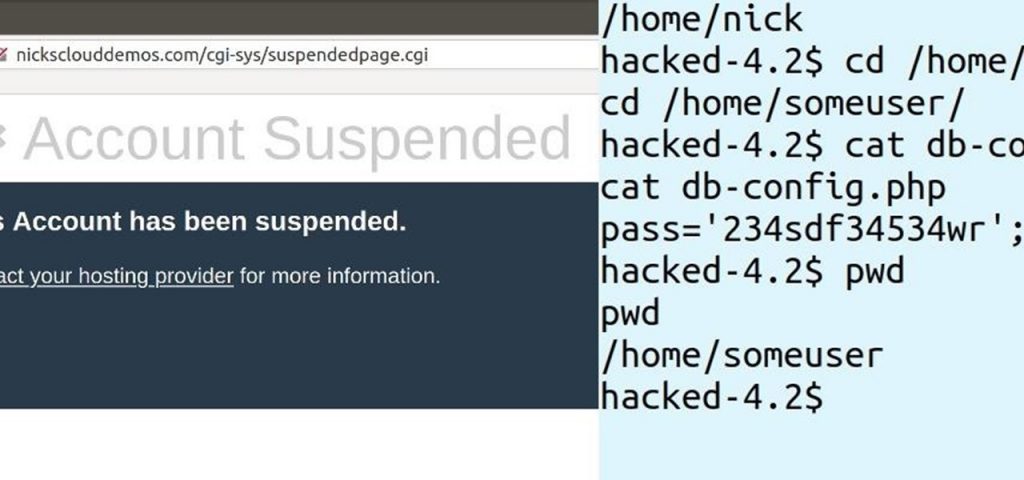
In recent weeks, several readers have asked us about how to develop a secure website. It should be noted that Internet security every day acquires greater relevance in the face of continuous development of computing and its vulnerabilities.
In this case, the hackers exploited a plugin vulnerability in WordPress to insert discrete scripts (programs) that use server resources. Thus several encoded files are hidden in the “ wp-includes ” and “ wp-content ” directories, in particular, and in sub-folders that are difficult to locate by security scanners.
This type of WordPress hacking is very common. The goal is to hack your server to use it either as a spam server or to use and redirect some of your traffic to other sites.
11 Tips to Secure Your cPanel Server
cPanel Server security is something that should never be overlooked. One day or another, there are chances that your server will be under attack and the integrity of your data will be at risk, not to mention that you may lose potential and existing customers at the same time.
Here are 11 things you can do to Secure Your cPanel Account against attacks:
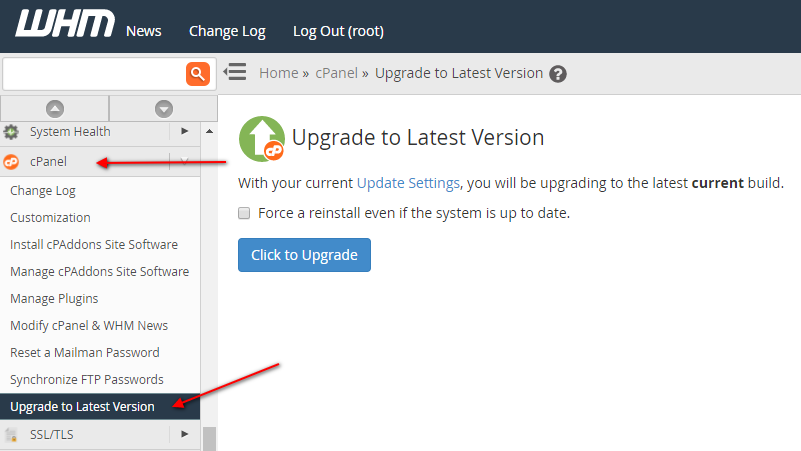
1. Keep Update cPanel
The first thing you want to do is make sure you have the latest version of cPanel. You can update cPanel by going to ” WHM> cPanel> Upgrade To Latest Version “. You can also achieve the same using this command line:
# /scripts/upcp –force
In order to have your server automatically updated, I recommend that you enable daily updates by going to ” WHM> Server Configuration> Update Preferences “:
2. Secure cPanel and WHM access
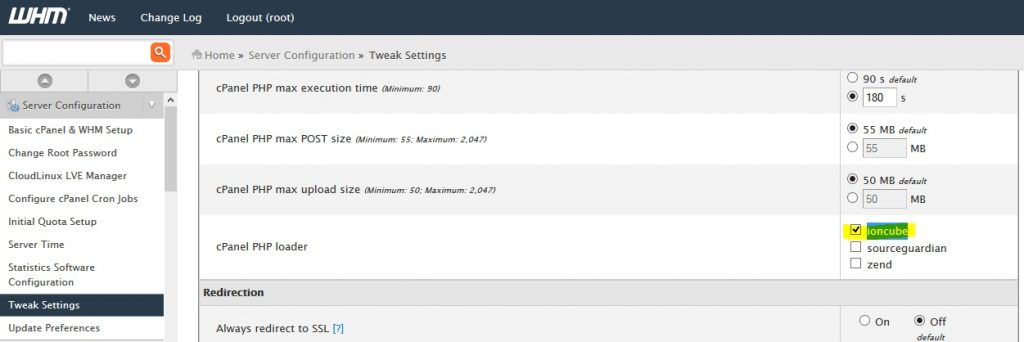
When you use an insecure connection to cPanel and WHM, your username and password are sent in clear text over the Internet. It is recommended to use SSL to secure all access to both control panels. From WHM, click on ” Server Configuration> Tuning Parameters ” and configure the redirect parameters as follows:
3. Secure SSH
SSH is among the services most vulnerable to brute force attacks. The default SSH configuration allows root access on the default port (22). Here’s how to secure the SSH daemon (process):
- Establish an SSH connection to your server and log in as root.
- Edit the SSH daemon configuration file:
# nano /etc/ssh/sshd_config
- Define a different port for incoming SSH connections by modifying this line:
Port 22
AT:
Port 22200
You don’t have to use port 22200 as mentioned above. Refer to this list of common TCP / UDP ports to find a port number for SSH that is not already in use.
- Disable the SSH root login by modifying this line:
#PermitRootLogin yes
AT:
PermitRootLogin no
- Save the file and restart the SSH daemon:
# service sshd restart
To gain root access via SSH, you must now log in as a normal user and then as a root by running the command:
# su – root
Note that you will first need to add the desired users to the wheel group (WHM> Security Center> Manage users of the wheel group).
4. Installing the SSL certificate on cPanel
The SSL certificate helps ensure that visitors to your website have access to a legitimate site and prevents sensitive data from being intercepted or tampered with in fraudulent ways.
The installation of the SSL certificate is done from the cPanel interface directly.
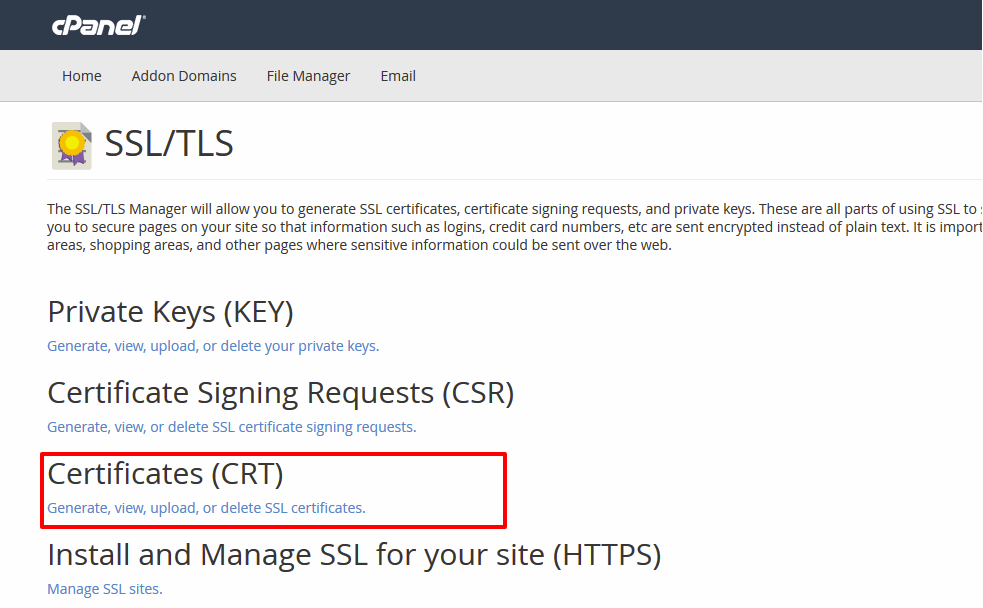
- Click on ” SSL/TLS ” in the ” Security ” section of your cPanel interface.
- Click on the ” Manage SSL sites ” tab.
- Fill in the ” Certificate (CRT) ” and ” Private key (KEY) ” boxes.
- If you do not have the BUNDLE file, you can leave this part empty. Click on ” Install a certificate ” to validate your request.
You are now able to install a paid certificate on your cPanel web hosting. The SSL certificate helps ensure that your visitors have legitimate access to your website. In addition, it allows a better SEO of your site.
5. Securing Apache and PHP
cPanel makes it easy to create and compile Apache and PHP using EasyApache. The first step in securing Apache and PHP is to update both components:
- Login to WHM and go to “ Software> EasyApache (Update) Apache “.
- On the first page, select “Old Configuration Backup” so that you can reuse your current server settings.
- Click on “Start personalization according to profile”.
- When prompted to select the Apache version to build, select the latest stable version. At the time of this writing, the latest version is 2.4.6.
- On the PHP Versions page, select the latest stable version (PHP 5.4.20 at the moment).
- On the next page, click on “Complete list of options”.
- Check the following options: Mod SuPHP, Mod Security and “Save my profile with the appropriate PHP 5 options …”. Leave the other options set as such.
- Click on “Save and Create”.
At this point, rebuilding Apache and PHP can take up to 30 minutes depending on your server speed.
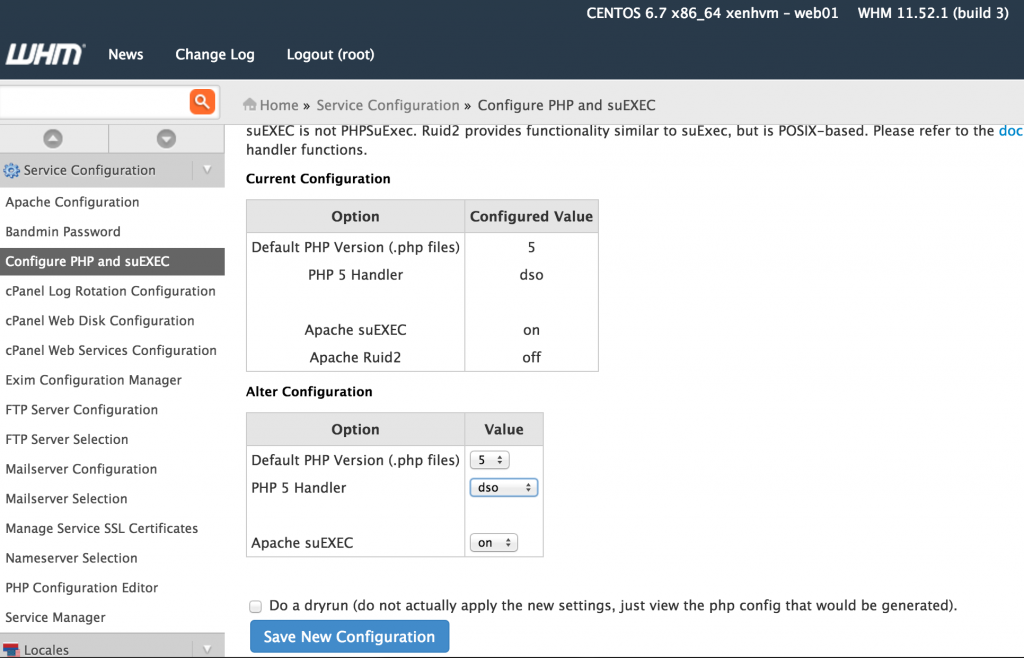
Next, you need to configure suPHP as the PHP manager. By enabling suPHP, files created by PHP scripts will be owned by the site user account instead of the account running the Apache process. To activate suPHP go to “WHM> Service configuration> Configure PHP and suEXEC“, select “suphp” and click on “Save new configuration”:
In order to prevent malicious PHP scripts from opening files outside of their home directory, it is recommended to enable open_basedir:
-
Log in to WHM and go to " Security Center> Security Center> PHP open_basedir configuration ".
-
Check the box "Activate open_basedir PHP protection".
- Click on “Save”.
The Apache server should restart automatically once this is done.
In order for open_basedir to work properly, you will need to create a file named “php.ini” for each account and place it in their “public_html” directory with the following content:
open_basedir = "/home/[utilisateur]/public_html/:/chemin/vers/autres/dossiers/"
This will prevent PHP scripts from accessing files outside of defined folders.
Finally, here are some recommended settings for PHP. Go to ” WHM> Service Configuration> PHP Configuration Editor ” and select “Advanced Mode”. Configure the following parameters:
- register_globals: Off
- disable_functions: show_source, system, shell_exec, passthru, exec, phpinfo, popen, proc_open, allow_url_fopen
Click “Save” when finished. The new settings will not take effect until you restart Apache. Go to “WHM Services> Restart> HTTP Server (Apache)“ to restart the service.
6. Disabling anonymous FTP access
To prevent anonymous users from uploading files to your server, go to “WHM> Service Configuration> FTP Server Configuration” and set “Allow Anonymous Logins” and “Allow Anonymous Uploads” to “No”.
7. Increase password strength required
You can force your users to use more complex passwords by going to ” WHM> Security Center> Password Security Level Configuration”.
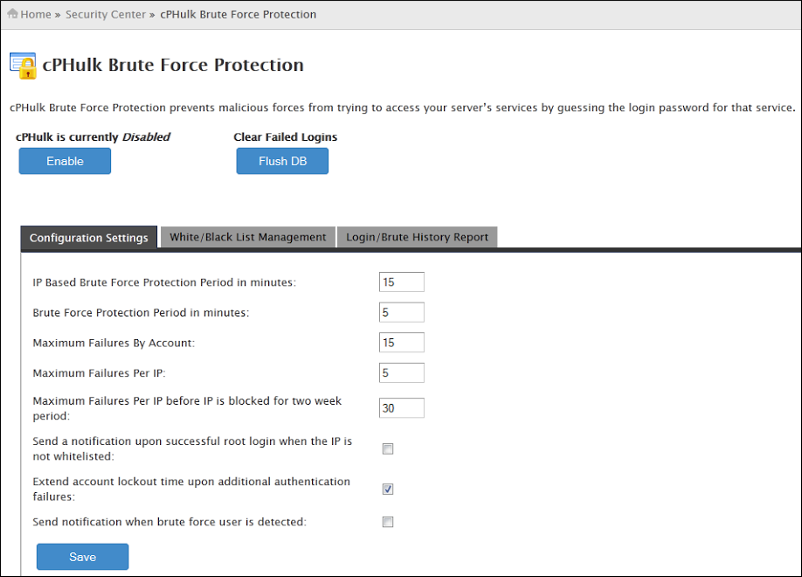
8. Activate cphulk
cPHulk protects your web servers from Brute Force attacks by blocking suspicious IP addresses for a predetermined period. To activate, go to “WHM> Security Center> cPHulk Brute Force Protection” and click “Activate”.
If you are connecting from a static IP address, you can add it to the cPHulk whitelist to avoid excluding yourself from your own server.
9. Install ClamAV antivirus
While Linux servers are not prone to as many viruses as Windows servers, it is nonetheless a good practice to install an antivirus. Even if your web server is not infected, it could still host a virus intended to infect visitors to your website.
ClamAV is available for cPanel servers as a plugin. Here’s how to activate it:
- Go to “WHM> cPanel> Plugins”.
- Select “Install and update” next to ClamAV and click “Save”.
- Once the installation of the ClamAV plugin is complete, refresh your WHM control panel so that the main menu is updated.
- Click on “WHM> Plugins> Configure ClamAV Scanner” and select all four (4) options:
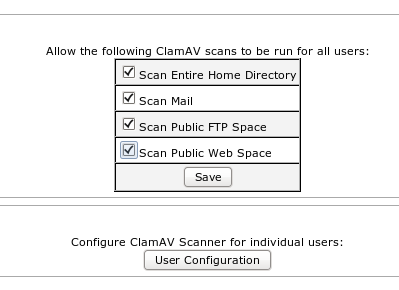
Click on “Save”.
10. Install a rootkit hunter
A “rootkit” is essentially a malicious computer program that runs on your server in “stealth” mode. The rootkit allows the attacker to gain root access to your server without you noticing.

In order to detect a rootkit on a cPanel server, you will need to install a rootkit scanner like the Rootkit Hunter:
- Log in to your server via SSH as a normal user and then become root:
# su – root
- Download the latest version of rkhunter from the below given link:
http://sourceforge.net/projects/rkhunter/files/latest/download?source=files
# wget http://downloads.sourceforge.net/project/rkhunter/rkhunter/1.4.0/rkhunter-1.4.0.tar.gz
- Extract the contents of the archive:
# tar xvzf rkhunter-1.4.0.tar.gz
- Start the installer:
# cd rkhunter-1.4.0# ./installer.sh –install
- Fill in the database properties of the file:
# rkhunter –propupd
- To scan for rootkits as root, run the following command:
# rkhunter –check
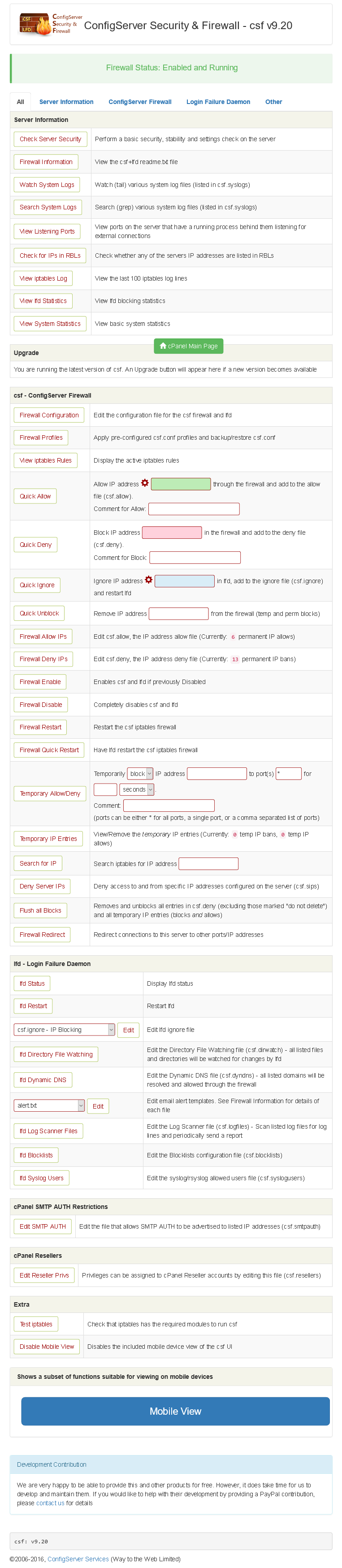
11. Install config server security firewall on Cpanel
This is perhaps the most critical part of shielding a cPanel server. One of the most popular firewall software for cPanel servers is ConfigServer Security and Firewall. CSF not only acts as a firewall by scanning various authentication log files, it will also scan your entire system and give you recommendations on what you can do to improve security.
Installing CSF is quite easy:
rm -fv csf.tgzwget http://www.configserver.com/free/csf.tgztar -xzf csf.tgzcd csfsh install.sh
Once you have installed CSF, go to “WHM> Plugins> ConfigServer Security and Firewall” and click “Test Server Security” for a list of tips for securing your web server.
Remember to open the new SSH port you defined earlier otherwise CSF will block it. To do this, go to “WHM> Plugins> ConfigServer Security & Firewall> Firewall configuration”. Find the parameter named “TCP_IN” and add the SSH port to the list.
Host And Protect offer a Real-time firewall to detect, block, and protect against hackers. In addition, it has some more advantages, since it integrates a powerful backup system that allows us to send the backups to other FTP servers or Dropbox.
It also allows us to enter the CMS facilities directly without having to search for the user and the password.
This means that HostAndProtect, in addition to being an excellent Web Hosting provider, is also very good for the management and administration from a single control panel.